When Research Meets Reality
How Threat-Actor Campaigns Cast a Shadow on Legitimate npm Binaries (and What IONSEC IR Sees in the wild)
1 · Executive summary
- North Korea’s latest “Contagious Interview” supply-chain wave dropped 35 typosquatted npm packages via 24 throw-away accounts, each hiding a hex-encoded loader (“HexEval”) that pulls an infostealer (BeaverTail) and optional back-door (InvisibleFerret). (socket.dev)
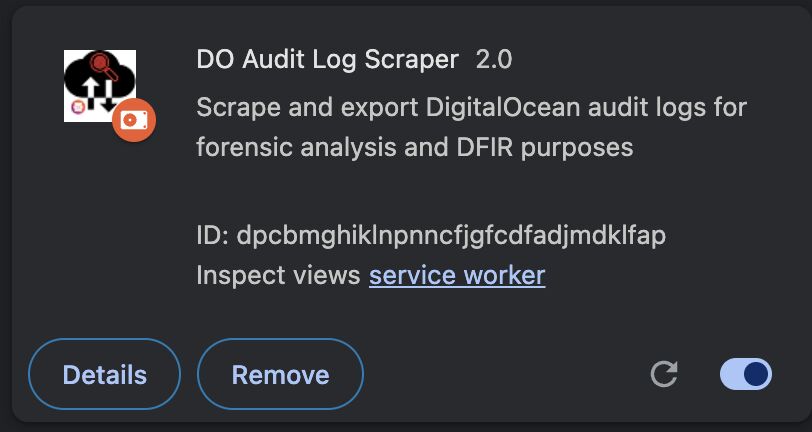
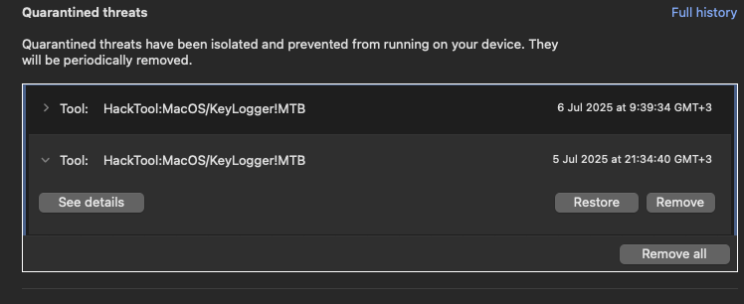
- To reduce friction, the operators embedded three unmodified binaries taken from the open-source node-global-key-listener project instead of writing their own key-logger.
- Security scanners now flag those hashes as PUA/key-logger even when they appear in legitimate software—showing how attacker reuse can stigmatise perfectly innocent code.
2 · Campaign snapshot
2025 Jun 25 Socket publishes technical write-up on 35 malicious packages (socket.dev) Jun 25 BleepingComputer amplifies the findings to wider industry (bleepingcomputer.com) Jun 25–Jul 05 Six packages remain live; download count tops 4 000 (socket.dev)
3 · Dual-use binaries: friend and foe
Platform Binary SHA-256 (legitimate & reused) Legitimate origin Windows WinKeyServer.exe e58864cc22cd8ec17ae35dd810455d604aadab7c3f145b6c53b3c261855a4bb1 node-global-key-listener v0.3.0 (npmjs.com) macOS MacKeyServer 30043996a56d0f6ad4ddb4186bd09ffc1050dcc352f641ce3907d35174086e15 idem Linux X11KeyServer 6e09249262d9a605180dfbd0939379bbf9f37db076980d6ffda98d650f70a16d idem
These helpers are byte-identical to those shipped for LaunchMenu’s productivity hot-key subsystem. The DPRK package simply copies them—turning benign utilities into IOC magnets.

4 · Fresh VirusTotal telemetry ( 5 Jul 2025 )
Metric Value Detection ratio 23 / 72 engines (trojan.keylogger, PUA, RiskTool) Community score –2 Last analysis ~1 hour ago (auto-rescan)

No engine labels the file as DPRK malware; all verdicts are capability-based (“key-logger”) or generic PUA, underscoring the context--not-hash principle.
5 · Why legitimate tools get flagged
- Static capability heuristics – hooking global keyboard APIs ≙ key-logger.
- Guilt-by-association – once a hash lands in IOC feeds, any appearance raises alarms.
- Unsigned binaries – OSS helpers rarely carry Authenticode signatures.
Dual-use deja-vu: remember plink.exe
Security teams already wrestle with PuTTY’s plink—an off-the-shelf SSH tunnel that turns into C2 plumbing in post-exploitation kits. Forums are full of admins begging AV vendors to stop crying wolf.
node-global-key-listener is walking the same tight-rope: perfect-fit utility inside LaunchMenu, perfect-fit spyware when sideloaded by an APT.
7 · Remediation & hardening checklist
Stop the bleed Remove all Socket-listed packages; purge caches (npm ci).
Restore trust npm audit fix --production; pin deps to vetted versions.
Erase footholds Full EDR scan; search for the three KeyServer hashes & “HexEval” string.
Rotate secrets All creds touched on suspect hosts (SSH, cloud, npm, GitHub).
Lock down supply chain Enforce MFA on npm/VCS, signed commits, SBOM/provenance (SLSA).
Limit blast radius Build & test in containers/VMs; least-privilege on CI agents.
Detect the next wave Feed Socket IOC set to SIEM; alert on outbound traffic to the three Vercel C2 domains.
Educate developers Simulate “fake recruiter + coding test” phishing; highlight typosquat clues.
Ensure recoverability Offline backups; quarterly restore drills.
8 · Key take-aways
- Hash ≠ intent. The same binary can log hot-keys for a launcher or exfiltrate credentials for Lazarus.
- Context decides enforcement. Where did it come from? Who launches it? What network traffic follows?
- Data-driven noise-surfing. Label legitimate high-risk capabilities as PUA, not APT-Flare-X. Reserve red banners for actual implants.
- IR teams need nuance. Slamming the “quarantine all” button breaks build systems and burns trust. Instrument first, block wisely.
About IONSEC Incident Response
From remote volatile-memory capture to one-click IaC rebuilds, IONSEC’s “Ready · Set · Respond™” method shrinks MTTR from days to hours—even when a “malware” alert turns out to be a misunderstood PUA. Need help separating real compromises from key-logger ghost stories? Reach out to IONSEC IR. (https://ionsec.io)
References
- Socket Threat Research blog, “North Korean Contagious Interview Campaign Drops 35 New Malicious npm Packages”, Jun 2025. (socket.dev)
- BleepingComputer, “New Wave of ‘Fake Interviews’ Use 35 npm Packages to Spread Malware”, Jun 25 2025. (bleepingcomputer.com)
- node-global-key-listener package page, npm registry. (npmjs.com)
- The Hacker News, “North Korea-linked Supply Chain Attack Targets Developers with 35 Malicious npm Packages”, Jun 25 2025. (thehackernews.com)